Hi! I'm Clemens Schotte,
Enthusiastic storyteller with a passion for technology
Enhancing your Azure Maps with a custom WebGL layer opens up a realm of possibilities for rendering dynamic 2D and 3D data. While Azure Maps provides a robust set of built-in features, there are times when you may require a more tailored solution. This is where the power of a custom WebGL layer shines.
WebGL, a cross-platform and royalty-free web standard, empowers you to harness low-level 3D graphics right in your web browser.
Introduction One of the requirements when building a business application, which may give access to private business data, is that only authenticated employees or agents be able to see that data. So how can you use Azure Maps in combination with authentication and authorization to ensure only the people that should be allowed have access?
Our Azure Maps docs describe in detail many different authentication scenarios but the complexity can make it seem difficult to implement.
Introduction When using Bing Maps for Enterprise in your solution/application, you need a Basic Key (limited free trial) or an Enterprise key to use the services. For example, you would add a Bing Maps Key to the script URL loading the Bing Maps Web Control like this:
1 <script src="https://www.bing.com/api/maps/mapcontrol?callback=GetMap&key={your bing maps key}"></script> Now your key is open text on your site source code and people who look can find and use your key.
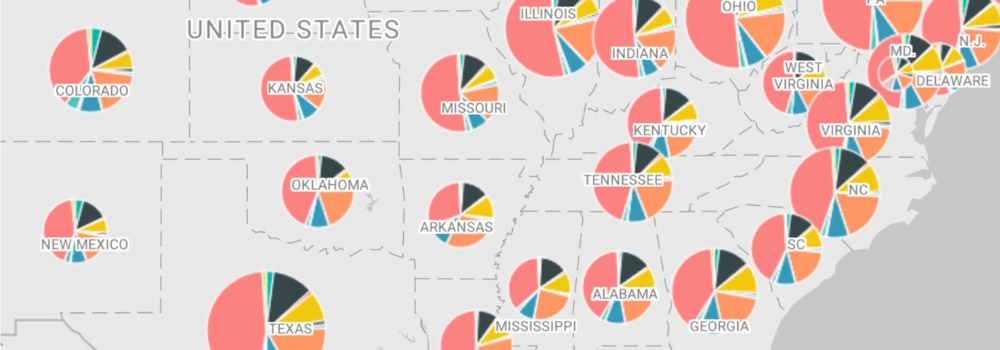
The Azure Maps Power BI Visual provides a rich set of data visualizations to enhance your data with location context. In the March release of Power BI, the Azure Maps visual introduces two new tools: Geocoding capabilities and a Pie Chart layer.
Geocoding in Power BI When dealing with data that has a location context, such as addresses or other geographic information, you might lack the precise point location (latitude-longitude) needed to plot these addresses on a map.
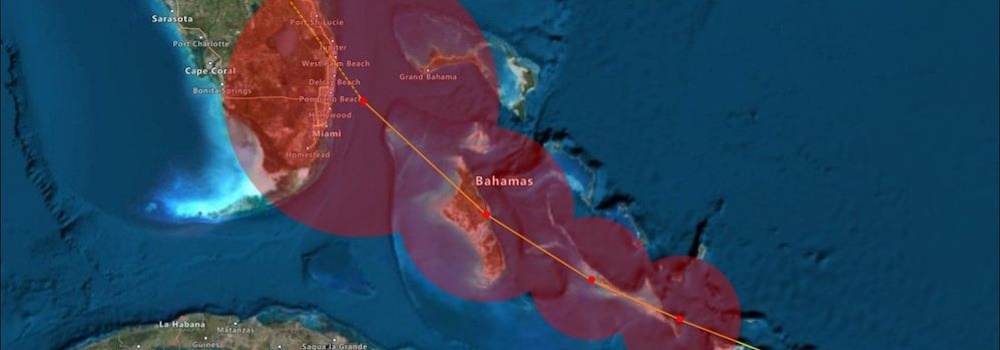
Azure Maps Weather Services, which became generally available in April 2021, has recently expanded its offerings with three new services: Historical Weather, Air Quality, and Tropical Storms. These additions empower developers and companies to enhance their capabilities when it comes to weather data.
Historical Weather The Historical Weather API provides actuals, normals, and records climatology data by day for a specified date range, up to 31 days in a single API request.
In many enterprise organizations, there are strict processes for privacy, access, and handling of personally identifiable information (PII). Azure Maps is a global Azure service, which means it is available worldwide (except for China and South Korea), but it also needs to store metadata and logs somewhere. In addition, Azure Maps Creator is an addon for private indoor maps that also holds map data. So, where do we keep this data?
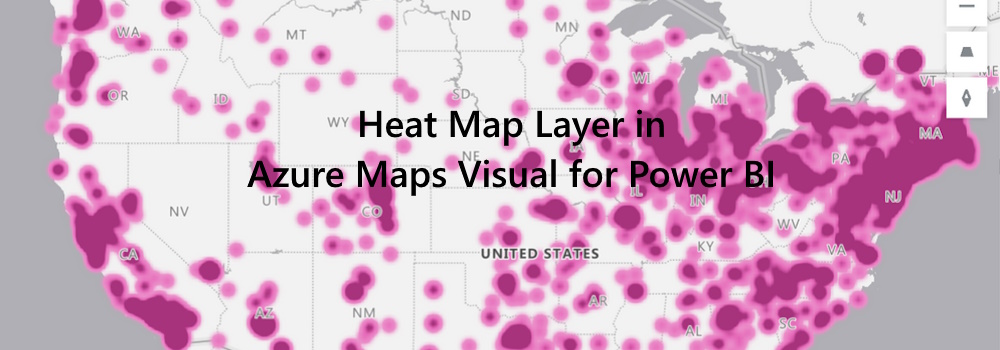
We are thrilled to announce the addition of the Heat Map layer option to the Azure Maps Visual in Power BI. This powerful feature allows you to visualize data density using various colors, highlighting data “hot spots” on a map. Whether you’re analyzing customer behavior, regional performance, or statistical trends, the heat map provides valuable insights.
Key Benefits of the Heat Map Layer in Power BI Data Density Visualization: Heat maps are ideal for rendering datasets with a large number of points.
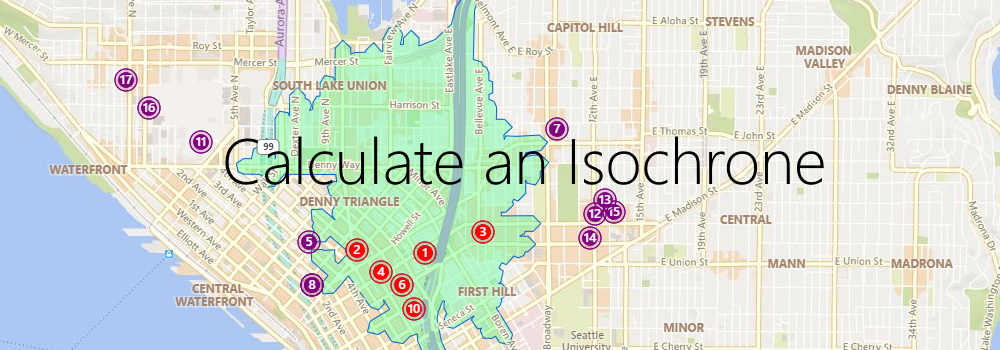
Imagine you are a store owner and would like to target customers that live within a 15-minute drive from your store with advertising for your weekly specials. You could draw a circle on a map, guessing that is about 15 minutes away, but it will not truly represent the time it will take for customers to get to your store. For example, a customer living near a major transit route can live further away from the store than a customer living in a less well-served part of the city.